Information Security Capabilities Redux
What was a capability?
We are using the easy definition of a capability. We are just say a capability is the ability to do something. It may be with technology, people, a natural resource, or combinations of all or more of those things.
For Information Security we are looking at the things we do for security and risk management. Or maybe more importantly the things we want to do.
Abilities for InfoSec
We can list out and group together all the behaviors we would expect for a particular domain. Since we are working on security we will see some obvious areas like network protection and anti-virus. There are many other areas that are not so obvious.
We look at what we have and what we want to do and assign each capability to some type of resource. The resource is the entity that actually does something. A real capability, in our modeling world, is just the behavior we want. It doesn’t really do anything by itself. That is why we need to know what resource we have that implements this capability. You may even have a software suite that can be assigned to several capabilities.
It may also be that we have a requirement but we don’t have a resource for that capability. That would lead to a gap in our security world.
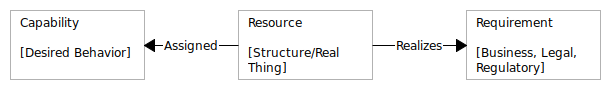
The reasoning or the requirement for a capability can even be as technical as a particular NIST/CSF control. Capability mapping can help define what technology or process has the ability to implement the control needed.
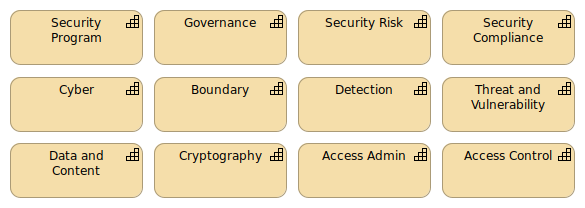
InfoSec
These are the highest level groupings for a typical Information Security department. It also is interesting that capabilities are not necessarily aligned by a People Manager. A capability may require resources that fall under multiple managers.
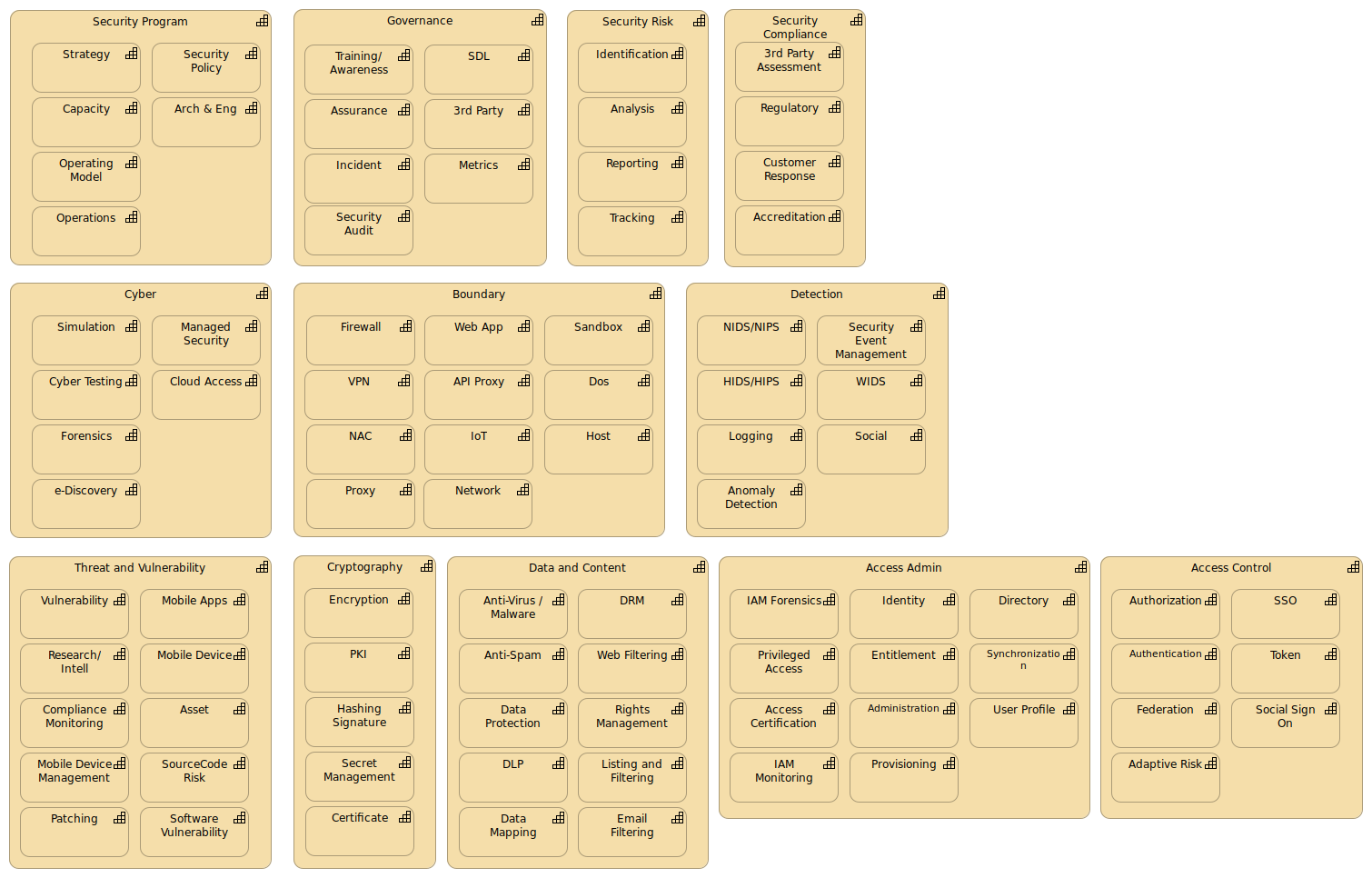
As we go to the next level down the number of abilities we need expands rapidly. The full security program is described here so you will see items for compliance and governance plus other non-operational functionality.
What can we do now?
Here are some common ways we can use this information to improve our work and increase our level of security.
- Justification, do you know why you need a capability - is there a requirement for it?
- Overlap, do you have multiple technologies that seem to do the same thing - build a Capability to Technology map to check for overlap
- Transparency, can you explain to a stakeholder how you meet business or regulatory requirements?
- Gap, do you have dangling capability that might be needed - build a capability map showing gaps
- Communications, how do you explain to the various people in your area how they are contributing to the bigger picture - capability mapping is the bigger picture
Summary
Our capability journey will continue as we build a real world example. Until then….
If you have any questions drop me a note @scmunk